Identity and Access Management (IAM) is core and key component of any cloud provider. To put it bluntly IAM deals with specifying who or what can access services and resources in AWS. Here Who - is AWS Identity and What - is IAM policy
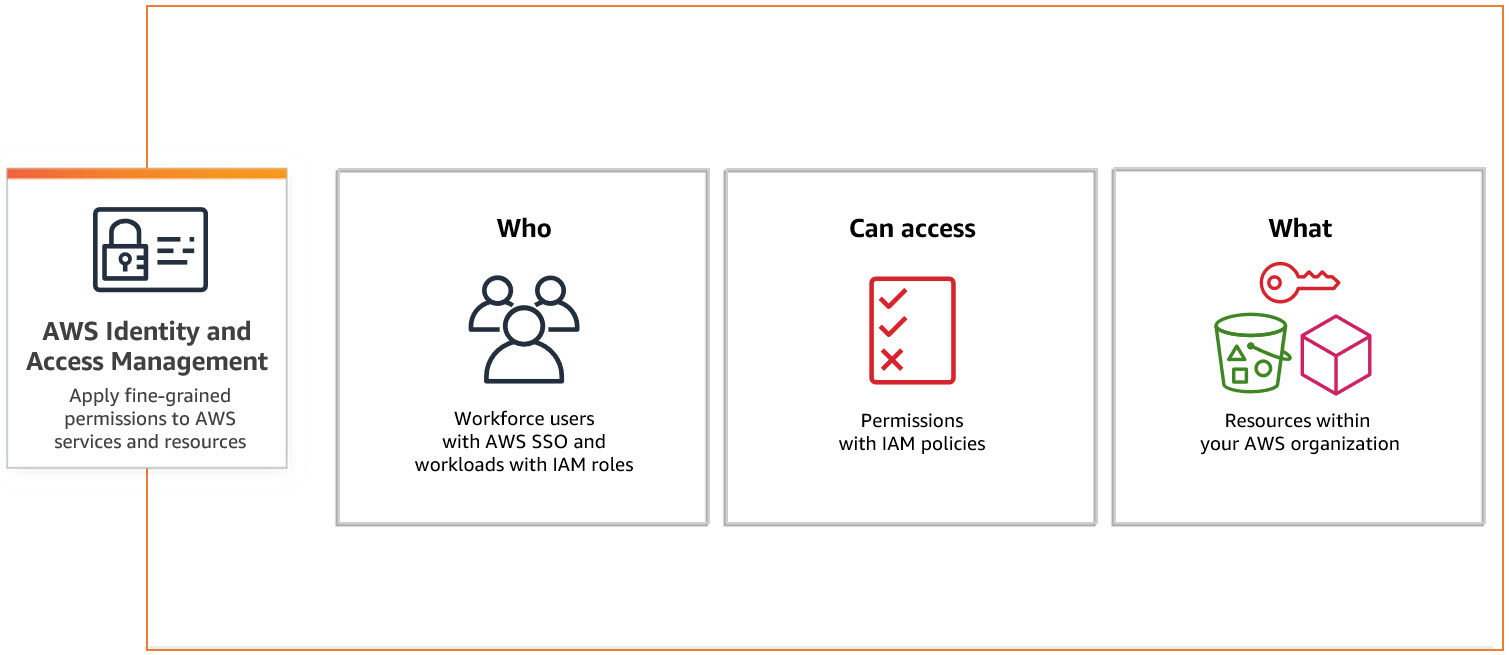
So What is Identity Then?.. AWS Identity:
Any AWS root user can create an Identity. An Identity can be user or workload that can be authenticated and authorized to perform actions in AWS.
Identities can be User, user group or a role.
Identity Types:
- User: single user
- User Group: collection of users
- Role: a blueprint of permissions can be associated with user or group or program
What is a IAM policy?
Each IAM identity can be associated with a policy(json file) determining the what actions can a user, role or member of user group can perform on which aws resources and under what conditions.
Lets first look at how a policy looks
Below is the example of Resourced Based Policy:
In Below policy we are describing the actions that can be performed on S3 Bucket
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Stmt1693315851336",
"Action": [
"s3:GetObject",
"s3:PutObject"
],
"Effect": "Allow",
"Resource": "arn:aws:s3:
::testbucket/*"
}
]
}It might look overwhelming if you are new to AWS IAM lets break it down.
Policy Terms:
Version: The Version policy element specifies the language syntax rules used by aws that are to be used to process a policy. There two possible values
- 2012-10-17
- 2008-10-17 2012-10-17 is latest policy version used by aws.
Statement: The Statement element is the main element for a policy. The Statement element can contain a single statement or an array of individual statements like Sid, Action, Effect ..etc
Each individual statement block is be enclosed in curly braces { }. For multiple statements, enclose them in array: [ {},{}.. ].
Sid (optional field): a unique identifier for your statement. this needs to be unique for each statement across the policy.
Action: Describes the actions to be performed on resource
Effect: To describe either to allow or disable the action.
Resource: The Resource element specifies the single aws Resource or multiple aws Resources that the statement covers.
There are many other policy terms that can be added to the depending upon the policy type.
There are many other policy types available in aws.
There are different Types of policies in AWS. The following policy types, listed in order from most frequently used to less frequently used.
- Identity-based policies
- Resource-based policies
- Permissions boundaries
- Organizations SCPs
- Access control lists (ACLs)
- Session policies
Below is the example for Resource based policy with Principal
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "NotPrincipalWithDeny",
"Effect": "Deny",
"Action": "s3:*",
"Principal": "*",
"Resource": [
"arn:aws:s3:::BUCKETNAME/*",
"arn:aws:s3:::BUCKETNAME"
],
"Condition": {
"ArnNotEquals": {
"aws:PrincipalArn": "arn:
aws:iam::444455556666:user/user-name"
}
}
}
]
}The above example shows a resource-based policy that can be used instead with Deny to explicitly deny all principals except for the ones specified in the Condition element.
What is Principal:
Principal can be AWS account, root user, IAM roles, IAM users and AWS Services.
These are useful when you need to enable cross account for a AWS resource like S3.
So different type of Policies are used with AWS IAM Identities and Resources to enable Identity and Access Management across aws.
Note:
root user: default user that comes with your aws account.